

Cyber-attacks on Australian businesses up 89%
31 Jul 2021, by Slade Baylis
The Covid-19 pandemic has forced many businesses to transition their workforce to remote working. For some staff, this could be as simple as accessing emails and cloud-based services from home. Alternatively it could require a more complete solution including VPN access to their company network, hosted phone solutions, and remote desktop software to access tools and devices hosted within their company’s IT infrastructure.
Whilst this shift to remote working has helped to protect staff, it has also moved the front-line of company infrastructure into their homes, meaning that many of these businesses are more vulnerable to web-based threat like viruses and malware than ever before. In addition, criminals have increasingly targeted vulnerable corporate systems over the internet.
In order to help protect our clients from this, we’ve put together some information on the common threats that organisations faced during 2020, as well as the threats they are likely to face moving forward so that they can better prepare for the challenges ahead and take action to protect their businesses.
Cyber-attacks on Australian businesses up 89%
With the shift to staff working remotely, it’s of no surprise that the amount of attacks against organisations have increased purely due to the larger attack surface; however, it may come as a shock that Australia is one of the leading countries when it comes to the increase of cyber-attacks against company systems since the shift to working remotely.
Since the start of the pandemic, attacks against Australian businesses have increased by up to 89%, second only to France who noticed an increase of 96%.
Increase of cyber-attacks as a result of working remotely
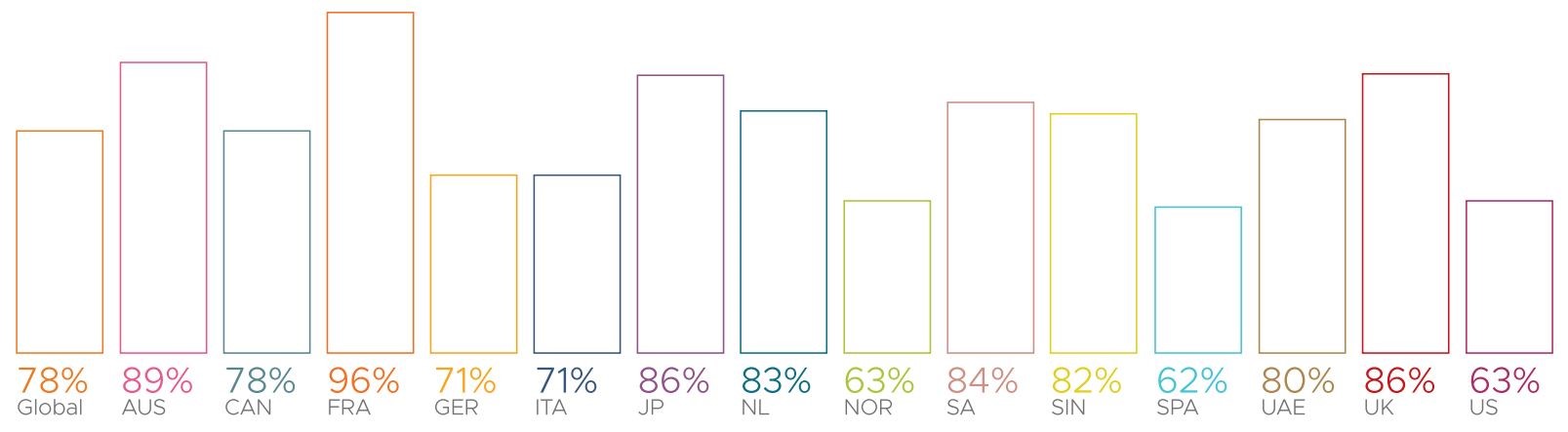
Source: Carbon Black – Global Security Insights Report 2021
Ransomware on the rise, as are the prices demanded
Ransomware has been and continues to be one of the biggest threats facing organisations. From an IT perspective, not only does it have the ability to shut down infrastructure and steal sensitive information, but often the damage such an attack does to an organisation and its reputation is even greater.
An increasingly common practice is the creation of Ransomware-as-a-Service (RaaS), which is effectively a business model where Ransomware hackers create different variants of Ransomware attacks that they then lease out/sell to cyber criminals, rather than use themselves.
With the ease of use of these new sorts of ready-made ransomware attacks, as well as the general increase in cyber-attacks across the board, so have the prevalence of Ransomware attacks against Enterprise organisations and even SMBs.
Not only has the number of attacks increased, but so has the amount that hackers are demanding should they gain access to business systems.
It’s been reported by cyber-security company Sophos that the average ransom payment just in Q4 of 2020 had increased by 21%.
The average ransom payment during that quarter was the equivalent of $233,817.30 USD, payable in cryptocurrency, compared with the average payout the year before, which was $84,116.00 USD.
Average ransom payouts, quarterly

Source: Sophos 2021 Threat Report
In addition to both the increased number of attacks across the board and the increased ransoms being asked for, a pattern has emerged among several ransomware “families” where they also extort their victims through threats of releasing confidential information to the wider public. This means that even if a company has a robust and reliable backup of their systems that they can restore from, they may still feel pressure to pay to avoid the release of their data.
Remote desktop protocols and services are prime targets
The software and protocols used to enable working remotely have become the prime targets of malicious actors who look to gain access to sensitive data and systems that businesses rely on.
Internet facing RDP servers have long been a favorite of criminals looking to gain initial access to business systems, with them receiving a never-ending barrage of brute-force attacks (most commonly associated with attempted ransomware attacks).
One of the threats that rose in 2020 was a ransomware-type exploit called Phobos which specifically targeted the Remote Desktop Protocol (RDP) to gain access to a network, through use of brute forcing, or taking advantage of insecure connections on port 3389. The Phobos exploit is one example of malware that was/is being sold via a RaaS model, increasing the likelihood of it being used out “in the wild” as even less-sophisticated malicious actors can utilise it.
So whilst Windows desktops and laptops were still the targets of choice throughout 2020, attacks on servers running both Windows and Linux saw a steady increase in the number of attacks against them. It’s anticipated that behavior is only going to increase moving forward
The first step to protecting your business
To be able to protect yourself from the threats all businesses are going to increasingly face, you first need to be able to know how your infrastructure may be vulnerable. Vulnerability scanning is a service that identifies the weaknesses in your systems so that you can get a sense of how well you are protected. An initial scan, allows you to take immediate corrective action to fix issues before they become a real problem. It’s important to continue scanning daily as new threats emerge and to fix issues before criminals find them.
To assist all our customers, Micron21 is pleased to announce its partnership with Qualys, winner of SC-Media’s 2020 vulnerability management awards1.
As a special offer, Micron21 is offering a free initial scan for customers hosting their own servers with us
If you are interested in learning more about vulnerability management or our cyber-security products, call us on 1300 769 972 (Option #1) and we can discuss different solutions for making you systems more secure.
You can also find more information about our Vulnerability Scanning offer via the link below:
https://www.micron21.com/vulnerability-scanning
1. https://www.qualys.com/company/newsroom/news-releases/usa/qualys-wins-best-vulnerability-management-at-sc-awards-2020/
