

Dangerous cyber-threats to look out for leading into 2023
28 Jul 2022, by Slade Baylis
With many businesses having adapted to Covid-19 restrictions by having staff work remotely, questions around the security of company infrastructure have been top of mind over the last few years.
The now ever-present threat of ransomware and the potentially crippling impact it can have on a business, is something that businesses now need to be on guard against on an ongoing basis - especially with the attack surface expansion that comes with more staff working from home. Recent geopolitical issues have had a big impact too. Attacks by state actors dramatically increased, targeting not only other Governments, but also organisations around the world with the aim of disrupting the international supply chain.
With all of these issues being new unique challenges that businesses need to know about and defend against, we’ve decided to put together a list of the biggest threats to keep an eye out for moving into 2023 and beyond. Our aim is to help ensure our customers are always one step ahead of these threats so that they can protect themselves against them.
Ransomware is one of the most disruptive cyber threats to both organisations and individuals
In our Cyber-attacks on Australian businesses up 89% article from 2021, we noted that that two new trends were developing relating to ransomware. The first was the creation and growing popularity of Ransomware-as-a-Service (RaaS) in which malware is created to automate ransomware attacks, which is then sold to third-parties – the ones whom actually get their hands dirty and carry out the attacks. The second trend was around an increase in the number of ransomware attacks globally, as well as an increase in the amount of money being demanded by these cyber-criminals. Unfortunately, both of these trends have continued into 2022 and are predicted to continue into 2023 and beyond.
For those who are unfamiliar, ransomware attacks are a type of attack whereby after gaining access to an organisation’s or individual’s systems, the malware encrypts all the information within the device and extorts the owner for a ransom to have that information decrypted. In addition, it’s also common practice for cyber-criminals to threaten to release the data to the public if the ransom is not paid, creating even more of a public relations disaster for any organisation that’s affected.
As reported by the Cybersecurity & Infrastructure Security Agency (CISA) in the US1, cyber security authorities in the United States, Australia, and the United Kingdom all observed an increase in sophisticated, high-impact ransomware incidents against critical infrastructure organisations globally. It was noted that “phishing emails, RDP (Remote Desktop Protocol) exploitation, and exploitation of software vulnerabilities” were the top three initial infection vectors for ransomware incidents in 2021.
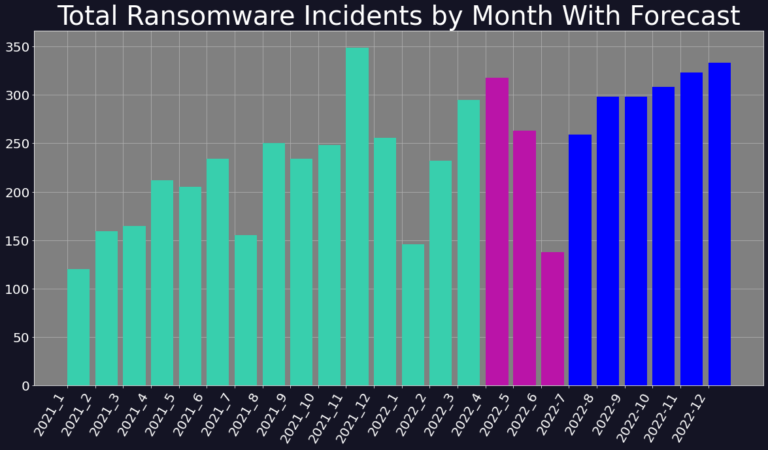
Source: Digital Shadows: Q3 2022 RANSOMWARE PROJECTIONS
These types of attack are likely to grow even more in frequency, as it was also noted that due to “the increase use of remote work and schooling” throughout 2020 and 2021 and the “expanded remote attack surface”, network defenders were left struggling to keep pace with routine software patching. With Gartner2 also reporting that currently 60% of knowledge workers are working remotely and that at least 18% of those will not return to the office, these threats are likely to continue to be an issue into the future.
In addition to the damage caused to an organisation through the loss of access to data and systems, attackers also began diversifying their approach to the extortion of their victims. It was also reported by CISA1 that after gaining access to and encrypting their victim’s networks, the ransomware threat actors also “increasingly used triple extortion”. This tactic was one in which the victim is threatened with the public release of the stolen information, disruption to their internet access, and/or the informing of the victim’s partners, shareholders, or suppliers about the incident. The purpose of this triple pronged approach is to apply as much pressure as needed in order to get the victim to pay the ransom demanded.
Due to the devastating consequences of a breach, it’s critical that individuals and businesses adopt strategies to mitigate these risks and protect against ransomware.
There is a heightened cyber-threat environment globally
Since the Russian invasion of Ukraine, there has been a rise in the number of cyber-attacks on government and military infrastructure globally. This shouldn’t come as much of a surprise, as back in 2010, The Economist3 declared that ‘warfare has entered the fifth domain: cyberspace’. However, it’s not just government infrastructure that’s feeling the heat from the increased cyber-threat level - it’s also organisations all over the world feeling the impact too - as state actors target key points in the supply chain globally.
As defined by Gartner4, a supply chain attack is when “goods, services or technology supplied by a vendor to a customer have been breached and compromised”, which then introduces risks to all of their customers. This can vary from a malicious actor using social engineering to break into an email account and using it to send out fraudulent emails or malware to their customer base, to even more frighteningly, a malicious actor modifying trusted software to potentially provide back-door access to their client’s business systems.
Gartner predicts that by 2025, 35% of organisations worldwide will have experienced attacks on their software supply chains, that’s a three-fold increase from 2021! Similarly Forbes5 also reported that organisations have seen increases in the number of attacks against their infrastructure, stating that in Q4 of 2021, businesses suffered 50% more cyber-attacks per week.
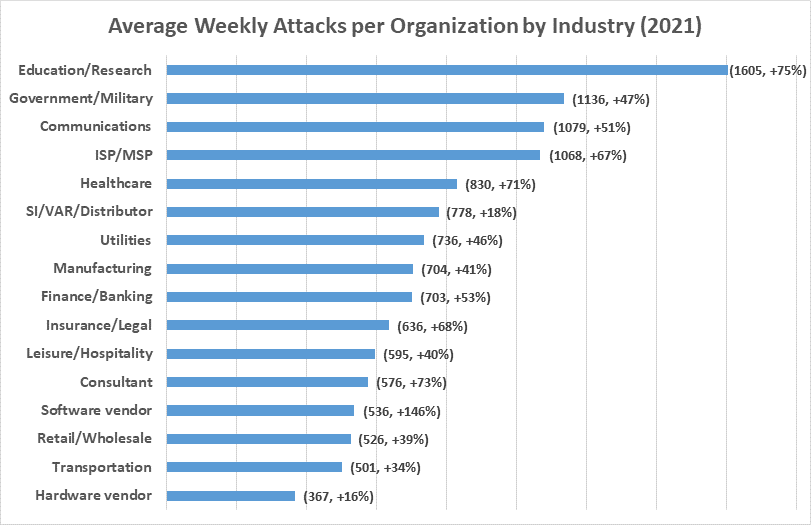
Source: Check Point Research: Attacks Increased 50% Year over Year
The reality of the increase of these threats is mirrored in the advisory put out by the Australian Cyber Security Centre (ACSC)6. In their advisory labelled “Australian organisations should urgently adopt an enhanced cyber security posture”, ACSC said that in response to the attack on Ukraine and the increased risk of cyber-attacks that “it is critical that Australian organisations are alert to these threats and take steps to adopt an enhanced cyber security posture and increase monitoring for threats.”
Malware Distribution Frameworks
As if the rise of RaaS wasn’t concerning enough, now a new method that’s being used to distribute malware could be even more concerning. As reported by Sophos7, one of the more unexpected developments on the cyber-security front came in the form of a new criminal service called Malware Distribution Frameworks. Unlike other forms of malware, this new service provides “a sort of criminal Content Distribution Network (CDN) similar in principle to those used by major internet portals but used exclusively for malware”.
In short, through utilising a massive network of pre-infected PCs, criminal groups are able to push their malware out to a large number of devices very quickly, massively increasing the rate at which new malware can spread across the internet. One of the many problems this creates for organisations is that “administrators and security teams will need to treat even minor malware alerts promptly, as any infection, no matter how seemingly insignificant, may simply be the start of a much more devastating cyber-attack”.
This development, in combination with the increased rates of staff working remotely on at least a part-time basis, highlights the need for remote management of any devices that staff use to access business systems. Within a world where more and more businesses adopt a hybrid work-from-home model, it will be through the use of Remote Monitoring & Management (RMM) tools that businesses will be able to maintain the security of their networks. Through use of these tools, IT administrators will be able to make sure that all the devices that staff use are up-to-date, as well as protected against malware through endpoint antivirus software.
Shotgun vs Targeted Attacks – Hybrid models are becoming the norm
In the past, cyber-attacks fell largely into two categories – that of widely distributed malware that isn’t targeted against any person or organisation in particular, and the other attack which is specifically designed to break into a specific organisation’s or individual’s network. The two types of attacks are colloquially referred to as “Shotgun Attacks" and “Targeted Attacks" respectively. A Shotgun Attack is designed to cast as wide a net as possible to infect as many devices as possible and thus is often an unsophisticated attack built around targeting the lowest common denominator. A Targeted Attack, on the other hand, can be much more devious. It requires that cyber-criminals do their homework prior, thus attacking organisations only after they’ve researched their target organisation, the people that work there, as well as determined whom in the organisation is most likely to be exploitable.
But now, an even more concerning attack is emerging that is a hybrid - Shotgun Attack with Pinpoint Targeting. Again as reported by Sophos7, one unfortunate development in 2021 was the emergence of hybrid approaches to Malware distribution, one in which malware is distributed widely in a largely untargeted manner, but only activates when certain conditions are met.
Whilst it might seem counter-intuitive for a virus to infect a device only to not take any action, from the perspective of the nefarious third-party, this approach actually has some benefits. Through not taking any action after compromising a device, they can stop “malware analysts from continuing to probe their servers, and they also reduce suspicion by keeping the number of attacks relatively low, under the radar that might otherwise tip off security researchers or IT admins to a wider campaign”.
Want to review your organisations cyber security?
With the knowledge of all the new threats on the horizon, it could be easy to fall into despair, however here at Micron21, we have a range of tools and techniques which can be used to secure your infrastructure. As experts in secure cloud we can help you review the security of your current systems, as well as work to improve it to help meet regulatory requirements or just give you peace of mind!
If you would like to know more, reach out to us via email at sales@micron21.com or via phone on 1300 769 972 (Option #1).
Sources:
- 1, 2021 Trends Show Increased Globalized Threat of Ransomware <https://www.cisa.gov/uscert/ncas/alerts/aa22-040a>
- 2, 7 Top Trends in Cybersecurity for 2022 <https://www.gartner.com/en/articles/7-top-trends-in-cybersecurity-for-2022>
- 3, War in the fifth domain <https://www.economist.com/briefing/2010/07/01/war-in-the-fifth-domain>
- 4, How to respond to a supply chain attack <https://www.gartner.com/smarterwithgartner/how-to-respond-to-a-supply-chain-attack>
- 5, Cybersecurity in 2022 – A Fresh Look at Some Very Alarming Stats <https://www.forbes.com/sites/chuckbrooks/2022/01/21/cybersecurity-in-2022--a-fresh-look-at-some-very-alarming-stats/?sh=4e46a5e66b61>
- 6, Australian organisation should urgently adopt an enhanced cyber security posture <https://www.cyber.gov.au/acsc/view-all-content/advisories/2022-02-australian-organisations-should-urgently-adopt-enhanced-cyber-security-posture>
- 7, Sophos 2022 Threat Report <https://www.cenet.com.au/files/sophos_2022_threat_report.pdf>
- 8, Ransomware in Q2 2022, Ransomware is back in business <https://www.digitalshadows.com/blog-and-research/ransomware-in-q2-2022-ransomware-is-back-in-business>
- 9, Check Point Research: Cyber Attacks Increased 50% Year over Year <https://blog.checkpoint.com/2022/01/10/check-point-research-cyber-attacks-increased-50-year-over-year>
