

Deep Dive – What is phishing, where did it come from, and how can you avoid it?
27 Feb 2023, by Slade Baylis
When it comes to cyber-security threats, the imagination instantly jumps to images of hackers wearing hoodies, in dark rooms lit only by the light of their monitors, tapping away on a keyboard at a mile a minute, breaking into online services through an overlooked flaw in their code. However, the reality is that the majority of cyber-security incidents don’t target glitches in software or obscure and hard-to-find vulnerabilities – they actually target people.
The reason for this is with software development practices maturing and the frameworks they are built with becoming more and more secure, in the majority of cases, one of the easiest ways of breaking in, is actually to try and fool actual people into sharing information they shouldn’t.
The term for this is “phishing” and due to it being one of the biggest threats to organisational security, it’s important you know what it is and how to protect yourself against it.
What is phishing and where did it originate?
Much like the occupation and sport that gives it its name, phishing is a type of attack that uses “lures” to trick people into providing information that they shouldn’t. They are called “lures” due to the different methods they use to try and trick their unsuspecting victims. For example, much like an actual fishing lure that attempts to trick fish into taking a bite by appearing like their normal food as much as possible - a “lure” in the world of cyber-crime also tries to appear as legitimate as possible in order to trick their target/s. They can take the form of emails pretending to be from popular online services like Facebook or Amazon, or instead be fake SMS messages about deliveries awaiting pickup, or could even take the form of fake online banking portals!
Cyber-criminals use these types of attacks to steal confidential information, such as login details to secure systems, online banking details, credit card information, and more.
Within Australia, phishing emails have been used by cyber-criminals to steal financial details for a number of years – and according to the Australian Cyber Security Centre (ACSC), phishing emails were actually first observed in Australia back in 2003. Unfortunately, they have become increasingly common and much more sophisticated since then. Globally though, the term "phishing" actually dates back all the way to 1996, where the term was used within an application called AOHell, which was designed to simplify computer hacking, or “cracking” as they called it back then.

Source: en.wikipedia.org
The name itself is derived from a combination of the words “fishing” and “phreak”. The term “phreak” is what some of the earliest hackers were referred to. In the beginning, a phreak was someone who engaged in “phreaking” - the act of studying, exploring, and ultimately experimenting with (often without permission) telecommunication systems. The term “phreak" itself was actually a contraction of the words “freak” and “phone”. Much like the early days of viruses – which we’ve covered in our recent article With 80% of malware evading antivirus applications, signature-based protection isn’t enough anymore – the early days of phreaking were also fairly benign, being limited to groups who had figured out how to re-route calls through using a series of different tones, so that calls could be made anywhere in the world for free. This community of “phone phreakers” even included the likes of future Apple co-founders Steve Jobs and Steve Wozniak!
Unfortunately, phishing itself didn’t start out this harmless, as one of the earliest implementations was within that some aforementioned application called AOHell - which enabled its users to try and deceive others in order to steal passwords and credit cards. As detailed by Cisco1, this service included a function called “CC/PW Fisher” which would message users of the AOL platform and attempt to get them to share that sensitive information. These messages were phrased to make the receiver think they were from legitimate sources, such as one message which claimed to be from AOL’s Customer Service department, stating that the receiver needed to reply with their login details in order to avoid being disconnected from the service.
As you can see from the above, even the earliest incarnations of phishing attacks attempted to use emotions like fear and urgency to compel their victims into making a mistake.
How does phishing work? Common tactics and different types of attack
When it comes to any sort of scam that relies on its victim making a mistake, they often have to attempt to use emotions such as fear, urgency, curiosity and greed. Phishing is no different, as it fundamentally needs a user to avoid looking at their “lures” with a critical eye.
Here are a few commonalities between phishing attacks:
- They frequently use emotions like fear, curiosity, urgency, and greed to compel their potential victim into opening attachments or click on links.
- They are designed to appear as legitimate as possible, attempting to appear to come from legitimate companies and individuals.
- They are becoming increasingly sophisticated – the days of being able to tell a legitimate email from a fraudulent one via looking for grammatical errors are almost gone.
- Unfortunately, it can potentially only take one successful attack to compromise your network and in turn have your data be stolen.
With these being the common attributes of any phishing attack, by keeping a watchful eye out for communication that has these characteristics, you can be on guard against them. For example, if you receive an email claiming to be from the ATO (Australian Tax Office) claiming that you have an unclaimed tax return and only need to click on a link to receive it, you should double-check the email for issues - as it’s highly likely to be fraudulent. In the same vein, if you receive an email claiming to be from the federal or state police claiming you have a fine that you are required to pay, it’s best to do the same.
In fact, taking extra precautions, even if it appears legitimate, is the best practice in most cases. For example, reaching out separately to the sender via their publicly accessible phone number is often recommended for any communication that is causing you worry or concern.
This sort of wide-net phishing, where these fraudulent emails are sent far and wide to as many recipients as possible, is only one type of phishing attack that exists.
Some of the different categories of phishing include:
- Email Phishing: By far, this is the most common type of phishing. This type of attack uses phony hyperlinks in legitimate-appearing emails to lure their recipients into sharing confidential information.
- Spear Phishing: Another play on the term fishing, “spear phishing”, as the name implies, is the act of phishing attempts that target specific individuals from an organisation. These attacks are often hand-crafted using information gathered through research into the personal and professional lives of staff. It can include making emails appear to be from colleagues, friends, or even close family members!
- Malware Phishing: This approach is similar to email phishing, however the information is not stolen by getting the recipient to enter it themselves - instead it gets the recipient to open trustworthy-looking attachments or links so that malware can be installed onto their device. Not only does this approach allow them to steal data, but it can even be the beachhead for a much larger ransomware attack.
- Whaling: Much like spear phishing, “whaling” also has a specific target in mind. However, the difference is that this term is usually used when it’s a “big fish” that is targeted, such as a large organisation, a business executive, or even a celebrity. In a similar way to spear phishing, these sort of attacks are tailored to their recipient, however with much more meticulous planning due to the even bigger payout they'll potentially receive should they succeed.
- Smishing: An increasingly popular form of attack is that of “Smishing”, which is a combination of the words “SMS” and “Phishing”. In these phishing attacks, an SMS is sent, often claiming to be from companies such as Amazon, or delivery services such as AusPost or StarTrack. Unfortunately, due to SMS messages often appearing more personal, this type of phishing attack is relatively more successful than the others.
The increasing sophistication of cyber-criminals – how phishing attacks are getting harder to avoid
With earlier forms of phishing, using common sense and checking for issues such as spelling mistakes, grammatical errors, or clearly incorrect hyperlinks, were usually enough to keep you safe. However, as with most forms of cyber-crime in recent years, in the pressure of an everlasting arms race between cyber-criminals and cyber-security vendors, phishing attacks are getting harder and harder to spot.
As reported by ZDNET2, hackers are going to greater lengths than ever before in order to trick victims into clicking malicious links and handing over sensitive information. Tactics such as mimicking real people, creating and updating fake social media profiles, and building up relationships built on “trust” over long periods of time before finally pulling the proverbial trigger on their attack. Each one of these dramatically increases the chances that their target will open an attachment or link containing a malicious payload or directing them to a fraudulent webpage.
As a recent example of that ever-increasing threat, big players in the international space have recently been caught up either enabling - or unintentionally abetting – phishing attacks across the web. As discovered earlier this month by Sentinel Labs3 (a well-known cyber-security company) - their analysts observed a new phishing campaign targeting Amazon Web Services (AWS) logins, but it’s the delivery method that’s the primary concern. Instead of utilising emails or SMS messages to deliver their phishing attack - which many people have largely grown accustomed to being wary of - this attack instead utilised online advertising platforms to get their malicious links in front of potential victims.
In this particular case, the attacks utilised Google Ads, one of the largest online advertising platforms, to get the phishing payload to display near the top of the Google search results. That prime real-estate is something that companies and individuals pay top dollar for - as it’s common for users to click on the first links they see in their results - so to have this be utilised to spread malware and steal information is particularly worrisome.
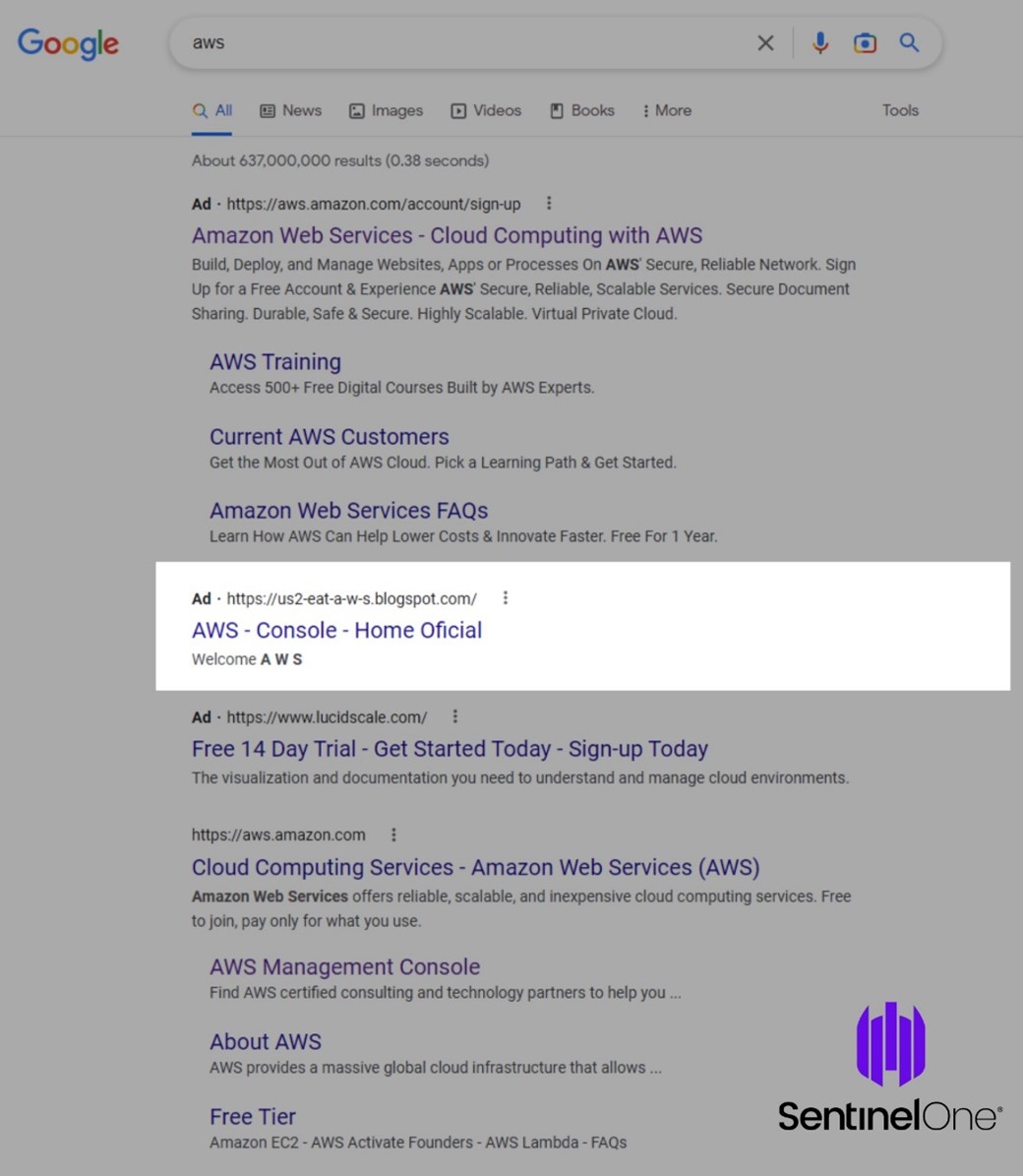
Source: SentinelOne - Cloud Credentials Phishing | Malicious Google Ads Target AWS Logins - Google Malvertising AWS Phishing Ad
Going back on the email front of phishing, another large organisation that was hit was Namecheap - an internationally-known ICANN accredited domain registrar and web hosting company. Earlier this month, their customers found themselves receiving a variety of phishing messages from official Namecheap email addresses, ultimately being sent via a third-party provider they used to send newsletters from called SendGrid. As reported by The Register4, in a since deleted tweet Namecheap were quick to name SendGrid as the culprit. However, SendGrid responded stating that the incident was “not the result of a hack or compromise” of their systems, and that they “encourage all end users” to deploy “security precautions such as two factor authentication and IP access management”. What this response seems to imply is that the cause of the issue may have been stolen access or API details that were used to log into or send emails through Namecheap’s official account with SendGrid.
Overall, what these incidents demonstrate is that phishing threats are becoming much more sophisticated. With this being the case, individuals and organisations alike need to take added precautions to ensure they don’t fall for phishing attacks, or worse yet, end up enabling them to be sent out in the first place!
What can you do to protect yourself? Utilise staff training and simulated phishing campaigns!
Unlike with regular software vulnerabilities, where the primary safeguards are to be found through utilising security appliances and making sure your systems are up-to-date, when it comes to phishing, your staff are your businesses' front line. Additional security services, such as improved email filtering – like with our IronPort service – can help reduce the amount of phishing attacks you receive via specific avenues, but overall, the battle against phishing is all about ensuring your staff are trained up on how to spot and avoid it.
It’s through regular staff training, keeping updated on the latest types of phishing attacks that are in use, and running “simulated phishing campaigns” to objectively measure your performance and compliance, that you can make sure you’re not vulnerable. Simulated phishing campaigns are strategies used to try and evaluate how well your staff know what to look out for, how incidents should be reported, and generally how to avoid phishing attacks.
At a basic level, the technique used to evaluate this compliance is to send specially crafted and fake phishing emails to your own organisation and staff. However, unlike real phishing campaigns, instead of the links within these emails being designed to deliver malware or to take people to fake login pages, these links just track information about who clicked on the link, which campaign they were fooled by and so forth. Whilst this may at first appear to be in bad taste – as you are fundamentally attempting to fool your own staff – it’s by detecting these potential mistakes yourself first, that you can help train staff further, in order for them not to be fooled by actual phishing attempts in the future.
Interested is phishing training, cyber-security audits, or simulated phishing campaigns?
If you are looking to find out where to begin, let us know! We can help audit your organisation’s cyber-security policies, procedures, and compliance with both. As part of that process, we can also help identify any gaps and make recommended changes in order to improve your organisation’s overall cyber-security posture.
We can help train staff on what phishing is, how to spot it, and help keep you up-to-date on current trends that are being seen “out in the wild” across the internet. In addition, utilising various tools from external suppliers, such as Sophos’ Phish Threat - we can also run simulated phishing campaigns in order to evaluate compliance across your staff, as well as help identify areas for further training. Using such tools, we are able to run simulated phishing campaigns modelled after the latest phishing threats being used, as well as provide in-depth reports on their results.
It’s through these approaches that you’ll be able to ensure your business isn’t the next one in the headlines after falling victim to yet another phishing attack!
Sources
1, Cisco, Phishing may feel like a recent term but the attack type is a decades-old scam <https://newsroom.cisco.com/c/r/newsroom/en/us/a/y2023/m02/security-history-the-evolution-of-phishing.html>
2, ZDNET, Phishing attacks are getting scarily sophisticated. Here's what to watch out for, <https://www.zdnet.com/article/phishing-attacks-are-getting-scarily-sophisticated-heres-what-to-watch-out-for>
3, Sentinel One, Cloud Credentials Phishing | Malicious Google Ads Target AWS Logins, <https://www.sentinelone.com/blog/cloud-credentials-phishing-malicious-google-ads-target-aws-logins>
4, The Register, Namecheap admits ‘unauthorized emails’ pwning its customers, <https://www.theregister.com/2023/02/13/namecheap>
